I have email account on grodno.net. Now google banned the workspace. How can I restore history? - Google Workspace Admin Community

Nisa Vithana, MBA (UK) on LinkedIn: “Least privilege" access is a cybersecurity principle that means giving…
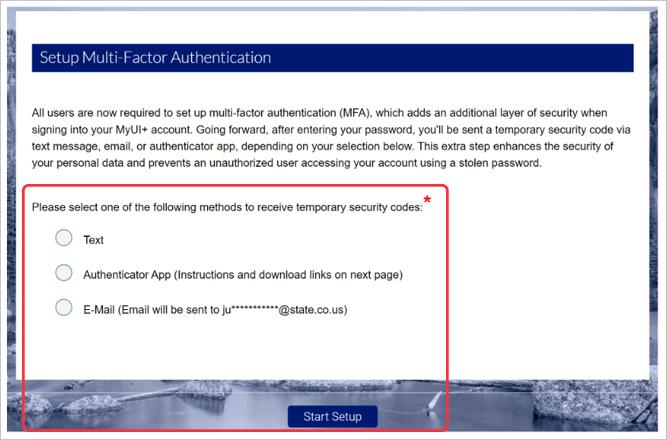
How to Register a New Third Party Administrator (TPA) Account in MyUI Employer+ | Department of Labor & Employment

Protect your digital systems from brute force attacks. | Pyramid Cyber Security & Forensic posted on the topic | LinkedIn









![Remove "Your ICloud Is Being Hacked!" Pop-ups [Virus Removal] - MalwareTips Blog Remove "Your ICloud Is Being Hacked!" Pop-ups [Virus Removal] - MalwareTips Blog](https://malwaretips.com/blogs/wp-content/uploads/2023/04/Your-iCloud-Is-Being-Hacked.jpg)